
Photo by Dan Nelson on Unsplash
Phishing and cyber-attacks are more prevalent than ever in today’s digital landscape, and while no organization can be 100% protected from cyber security threats, there are measures and processes that can be put into place to mitigate the risk of falling victim to a potentially devastating cyber-attack.
We’ve put together a check list to help you assess your organization’s IT cybersecurity strategy.
1. Create an overall cybersecurity strategy.
Don’t just focus on IT. Cybersecurity is a company-wide risk, so planning at the business level helps ensure that the entire company is prepared for an event, not just IT.
2. Develop an effective IT incident response plan.
Having an incident response plan in place helps to ensure staff can effectively respond to threats or incidents to minimize any damage while also making the recovery process more streamlined since everything is spelled out.
3. Consistent employee education on cyber security issues.
Providing year-round training on spotting phishing emails and reminding employees not to click links in emails is only the beginning. We suggest highlighting global threats that hit the news to help drive the point home that these things can impact anything at any time.
4. Build a consistent OS patching program.
Updates are typically deployed to patch new vulnerabilities found in operating systems and software, so keeping your OS up to date is paramount to a good cyber security program. This can be done with native OS tools such as, Windows Automatic Updates, or through other tools to manage patching at a global level for an entire organization.
5. Enforce strong passwords and maintenance of those passwords.
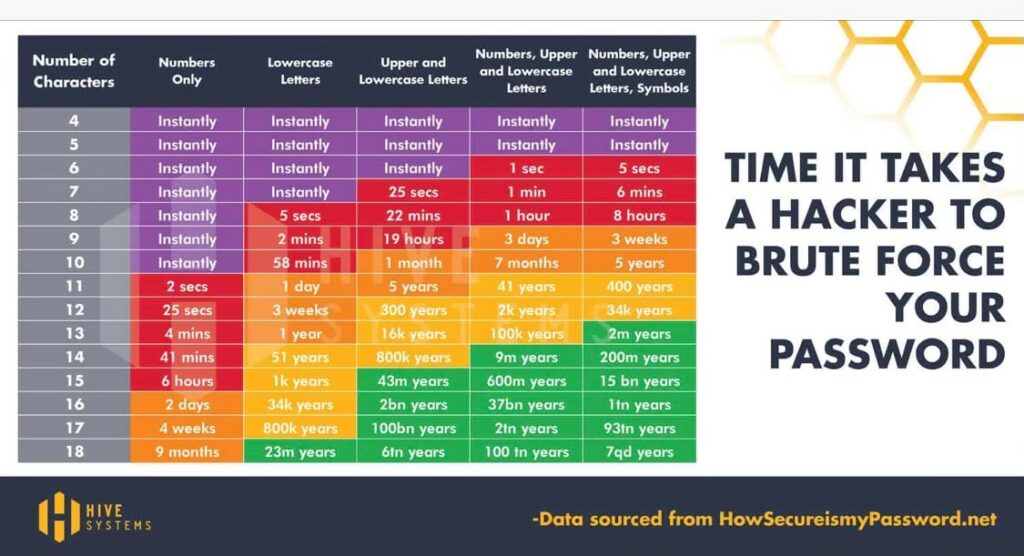
Looking at the chart below, it’s easy to see that the more complex a password, the less likely it will be compromised. Complex passwords are only part of the equation. Not re-using the same password helps ensure that one re-used password doesn’t expose the organization or yourself to unnecessary cybersecurity risk.
6. Force secure connections to the company network.
Staff should only be connecting to the corporate network remotely using company-owned devices that are secured with a client VPN software. They should be taught to avoid websites that don’t use SSL to secure them. These are easy to spot since most modern web browsers show a lock symbol in the address bar if the site is secured.
7. Maintain good backups of data.
If a company doesn’t have a good backup strategy, recovering from a cyber-security incident becomes even harder since there is risk for data loss. Backups should be isolated in a way that makes it impossible for threat actors to access and potentially exfiltrate and/or encrypt that data as part of a ransomware threat.
8. Keep anti-virus/EDR software up to date.
Most of these software packages auto-update, but that should be reviewed periodically to ensure timely updates are being applied not only to detection signatures but to the software itself to ensure its ability to react to a threat.
9. Limit administrative access to the network.
No company employee outside of IT should have any administrative access to IT infrastructure. Don’t give staff administrative rights over their own devices. This ensures staff can’t make changes to devices without IT’s knowledge, which helps keep the environment safer overall since only known good applications are being installed by IT as needed.
10. Enforce device lockout policies on any company-owned device.
Idle computers (i.e., unused for more than 10 minutes) should lock the screen so that someone can’t walk up to a company-owned device and start using it without authorization while also ensuring that people snooping around can’t see what is displayed on the screen in the event the user walked away.
11. Secure disposal of equipment and devices.
Devices that are no longer able to be used effectively shouldn’t just be tossed in the garbage. Physical destruction of hard drives after being formatted is critical to ensure data cannot be recovered.
12. Utilize 3rd party vulnerability scanning and penetration testing services.
Using these services from an outside vendor, like Calyx, ensures impartiality while also helping highlight potential security vulnerabilities before they are exploited by threat actors.
